Wireless network security. The type of wireless security and encryption. Which one to choose
Wireless Security
The availability of equipment and ease of organization are making wireless local area networks increasingly popular. The use of wireless networks is not limited to small offices and home systems. Large companies use Wi-Fi to connect to corporate network resources in places where laying cables is technically impossible.
However, the device decision demon wired network is not always justified, especially since in many cases too little attention is paid to the security of such networks. Experts estimate that almost 70 percent of successful hacker attacks over wireless networks are associated with incorrect configuration of access points and client software.
For some inexplicable reason, wireless network organizers often believe that turning them on automatically ensures the appropriate level of security. Equipment manufacturers, in turn, set low “default” security settings, or disable them completely, so that when deploying a network, clients do not accidentally encounter inability to access. At minimum settings safety equipment is best compatible with the most wide range other devices and almost any modern software. Therefore, after setting up and checking the network for compatibility with the existing infrastructure, the system administrator must change the security settings in order to prevent unauthorized penetration into the corporate network.
Unlike wired networks, wireless networks require increased attention to security, since they are much easier to penetrate, since this does not require physical access to the channel. Radio waves can be received by any compatible device, and if the data is not protected, anyone can intercept it. Of course, you shouldn’t give up passwords and other traditional means of authorization, but they are clearly not enough to protect against unauthorized access. Let's briefly consider several ways to increase the security of wireless networks.
A sequence of numbers and letters called the SSID (Service Set Identifier) is a unique identifier for your wireless network. Network ID transmission is a built-in security feature included by default in most equipment sold today, and it makes it easy to discover existing access points during network deployment. Transferring the SSID is required precisely so that your equipment can connect to the network.
Access points that are base stations for computers connected to the network, are a potential weak point through which an attacker can penetrate the network. There is no default authorization system at the access point level, which makes internal networks unsecured, so system administrators must implement the existing corporate system in wireless base stations.
To ensure increased security You can prevent access points from broadcasting the network ID. At the same time, the ability to connect to the network remains only for those who know the correct SSID, that is, employees of your company, and random users who discovered your network through scanning simply will not be able to access it. Disabling SSID transmission is possible in the vast majority of devices from leading manufacturers, which allows you to actually hide your network from strangers. If your network does not transmit identifiers, and if you do not advertise the use of wireless technology, then you will complicate the task of attackers. Detailed instructions for disable SSID These are usually found in the user manuals for wireless access points or routers.
Data encryption, which has long been used when sending important electronic correspondence, has found application in wireless networks. To protect data in equipment for wireless communication Various cryptographic algorithms have been implemented. When purchasing equipment, it is important to make sure that it supports not only low-level 40-bit encryption, but also high-strength 128-bit encryption.
To enable cryptographic protection you can use the following systems: “wired equivalent privacy” WEP (Wired Equivalent Privacy) or “Wi-Fi Protected Access” WPA (Wi-Fi Protected Access). The first system is less secure because it uses static (permanent) keys. Networks protected by this protocol are hacked by hackers without much difficulty - the corresponding utilities are not difficult to find on the Internet. However, according to experts, even this protocol is not used in more than half of operating corporate wireless networks. One of the ways to improve the effectiveness of WEP is to regularly automatically change keys, but even then the network is not 100% secure. Attempts to penetrate such a network will be left only to random people who discover it, but WEP will not stop malicious specialists, therefore, to fully protect corporate networks this protocol cannot be used.
In the recent past, wireless network organizers had no choice but to use the WEP protocol, support for which remains in modern devices both to ensure equipment compatibility and to ensure at least a minimum level of security in case it was impossible to use more modern protocols. Today, WEP is implemented in two modifications: with 64- and 128-bit encryption. However, it would be more correct to talk about keys of length 40 and 104 bits, since 24 bits of each key contain service information and do not in any way affect the strength of the code. However, this is not so important, since the main disadvantage of WEP is static keys, to select which attackers only need to scan the network for a certain time, intercepting transmitted information.
A more or less acceptable level of security can only be achieved by regularly changing keys and using 128-bit encryption. The frequency of key changes depends on the frequency and duration of connections, and it is necessary to ensure a secure procedure for transferring new keys to those employees who access the wireless network.
More effective encryption is provided by the WPA protocol, which implements dynamic key creation, which eliminates the possibility of interception or selection of the key, as well as an identification system (login-password) when connecting to a network based on the EAC protocol (Extensible Authentication Protocol). . In the WPA protocol, 128-bit keys are automatically generated for every ten kilobytes of data transmitted, and the number of these keys reaches hundreds of billions, which makes it almost impossible to select using scanning, even with a proven technique for intercepting information. In addition, this protocol implements the MIC (Message Integrity Check) data integrity checking algorithm, which prevents the possibility of malicious modification of the transmitted data. But special attention should be paid to the choice of passwords: according to experts, to ensure a high level of security, the password length should be at least 20 characters, and it should not be a set of words or some kind of phrase, since such passwords are easily opened by dictionary guessing.
The problem with WPA is that it was officially included in the IEEE 802.11 specifications only in mid-2004, so not all wireless equipment is capable of supporting this standard. Moreover, if there is at least one device on the network that does not support WPA, simple WEP encryption will be used, even if WPA is taken into account in the settings of all other equipment.
However, the equipment is constantly being improved and modern devices support a new, even more secure version of WPA2, working with dynamic keys of 128, 192 and 256 bits in length. Wireless communication technology itself is by its nature less protected from outside interference, therefore, when organizing such networks, it is especially important to make it as difficult as possible for unauthorized penetration into them. Among the pure technical methods the most effective is to reduce the power of the transmitted signal, because radio waves easily overcome the walls of buildings, and in rural flat areas they can travel very long distances. Attackers can park their car next to the building where your office is located and, in a comfortable environment, slowly pick up the key to your network. Therefore, it is important to adjust the signal strength so that it does not penetrate beyond the boundaries of your territory.
802.11i wireless security provides guidelines regarding authentication, user authorization to gain access to the network, and data privacy through encryption.
In conclusion, we present the main advantages and disadvantages of wireless networks in comparison with their wired competitor. Advantages of a wireless network:
Wireless networks allow you to save money when installing cable network, if it is impossible to organize wired access they are practically no alternative.
Wireless networks provide a high degree of user mobility; free movement within the same domain is possible. Another advantage is the ability to quickly deploy and move the network. The connection speed is quite high and comparable to wired solutions; with proper design, it is possible to provide the necessary bandwidth for data transmission, video, telephony.
Disadvantages of a wireless network:
The security of a wireless network is significantly lower than that of a wired network, modern standards such as WEP, 802.11i, etc. Although they increase it, the physical nature of the wireless network is such that the use of this technology for critical applications is not recommended.
The performance of a wireless network depends on the environment. Any objects located in the path of the radio signal reduce its power; interference is possible in the operating range from household appliances, the most typical of which are microwave ovens.
To protect your Wi-Fi network and set a password, you must select the type of wireless network security and encryption method. And at this stage, many people have a question: which one to choose? WEP, WPA, or WPA2? Personal or Enterprise? AES or TKIP? What security settings will best protect your Wi-Fi network? I will try to answer all these questions within the framework of this article. Let's consider everything possible methods authentication and encryption. Let's find out which Wi-Fi network security parameters are best set in the router settings.
Please note that security type, or authentication, network authentication, security, authentication method are all the same thing.
Authentication type and encryption are the main security settings wireless wifi networks. I think that first we need to figure out what they are, what versions there are, their capabilities, etc. After which we will find out what type of protection and encryption to choose. I’ll show you using the example of several popular routers.
I highly recommend setting up a password and protecting your wireless network. Set the maximum level of protection. If you leave the network open, without protection, then anyone can connect to it. This is primarily unsafe. And also an extra load on your router, a drop in connection speed and all sorts of problems with connecting different devices.
Wi-Fi network protection: WEP, WPA, WPA2
There are three protection options. Of course, not counting "Open" (No protection).
- WEP(Wired Equivalent Privacy) is an outdated and insecure authentication method. This is the first and not very successful method of protection. Attackers can easily access wireless networks that are protected using WEP. There is no need to set this mode in the settings of your router, although it is present there (not always).
- WPA(Wi-Fi Protected Access) is a reliable and modern type of security. Maximum compatibility with all devices and operating systems.
- WPA2– a new, improved and more reliable version of WPA. There is support for AES CCMP encryption. At the moment, this is best way Wi-Fi protection networks. This is what I recommend using.
WPA/WPA2 can be of two types:
- WPA/WPA2 - Personal (PSK)- This the usual way authentication. When you only need to set a password (key) and then use it to connect to a Wi-Fi network. The same password is used for all devices. The password itself is stored on the devices. Where you can view it or change it if necessary. It is recommended to use this option.
- WPA/WPA2 - Enterprise- a more complex method that is mainly used to protect wireless networks in offices and various establishments. Allows for a higher level of protection. Used only when a RADIUS server is installed to authorize devices (which gives out passwords).
I think we have figured out the authentication method. The best thing to use is WPA2 - Personal (PSK). For better compatibility, so that there are no problems connecting older devices, you can set the WPA/WPA2 mixed mode. This is the default setting on many routers. Or marked as "Recommended".
Wireless Network Encryption
There are two ways TKIP And AES.
It is recommended to use AES. If you have older devices on your network that do not support AES encryption (but only TKIP) and there will be problems connecting them to the wireless network, then set it to "Auto". TKIP encryption type is not supported in 802.11n mode.
In any case, if you install strictly WPA2 - Personal (recommended), then only AES encryption will be available.
What protection should I install on my Wi-Fi router?
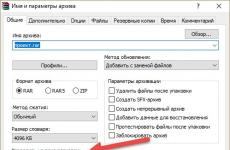
Use WPA2 - Personal with AES encryption. To date, this is the best and most safe way. This is what the wireless network security settings look like on ASUS routers:

And this is what these security settings look like on routers from TP-Link (with old firmware).

More detailed instructions for TP-Link you can look.
Instructions for other routers:
If you don’t know where to find all these settings on your router, then write in the comments, I’ll try to tell you. Just don't forget to specify the model.
Since older devices (Wi-Fi adapters, phones, tablets, etc.) may not support WPA2 - Personal (AES), in case of connection problems, set the mixed mode (Auto).
I often notice that after changing the password or other security settings, devices do not want to connect to the network. Computers may receive the error "The network settings saved on this computer do not meet the requirements of this network." Try deleting (forgetting) the network on the device and connecting again. I wrote how to do this on Windows 7. But in Windows 10 you need .
Password (key) WPA PSK
Whatever type of security and encryption method you choose, you must set a password. Also known as WPA key, Wireless Password, Wi-Fi network security key, etc.
Password length is from 8 to 32 characters. You can use letters of the Latin alphabet and numbers. Also special characters: - @ $ # ! etc. No spaces! The password is case sensitive! This means that "z" and "Z" are different characters.
I don't recommend betting simple passwords. It's better to create strong password, which no one will be able to pick up, even if they try hard.

It is unlikely that you will be able to remember such a complex password. It would be nice to write it down somewhere. It’s not uncommon for Wi-Fi passwords to be simply forgotten. I wrote in the article what to do in such situations: .
If you need even more security, you can use MAC address binding. True, I don’t see the need for this. WPA2 - Personal paired with AES and complex password- quite enough.
How do you protect your Wi-Fi network? Write in the comments. Well, ask questions :)
Since wireless networks use radio waves, the quality of the network depends on many factors. The most striking example is the interference of radio signals, which can significantly degrade throughput and the number of supported users, up to the complete impossibility of using the network. The source of interference can be any device that emits a signal of sufficient power in the same frequency range as the access point: from neighboring access points in a densely populated office center, to electric motors in production, Bluetooth headsets and even microwaves. On the other hand, attackers can use interference to launch a DoS attack on the network.Aliens operating on the same channel as legitimate access points not only allow access to the network, but also disrupt the functionality of the “correct” wireless network. In addition, to carry out attacks on end users and to penetrate the network using an attack Man-In-The Middle attackers often jam access points of a legitimate network, leaving only one - their access point with the same network name.
Connection
Besides interference, there are other aspects that affect the quality of communication in wireless networks. Since the wireless environment is a medium with shared access, each misconfigured client, or failed access point antenna can create problems, both on the physical and on the link level, leading to a deterioration in the quality of service for other network clients.What to do?
In summary, wireless networks give rise to new classes of risks and threats that cannot be protected from using traditional wired means. Even if Wi-Fi is formally prohibited in an organization, this does not mean that one of the users will not install a stranger and thereby reduce all investments in network security to zero. In addition, due to the nature of wireless communications, it is important to control not only the security of the access infrastructure, but also to monitor users who may become the target of an attack by an attacker or who may simply accidentally or intentionally switch from corporate network to an unsecured connection.security Add tags
Purpose: Bluetooth is a wireless technology that provides wireless transmission data over short distances between mobile personal computers, mobile phones and other devices in real time, both digital data and audio signals.
Principles of construction and operation of Bluetooth: At the core Bluetooth technology lies the combination of devices in piconets, which are small wireless data networks in terms of the number of elements (usually the network is built on the basis of two elements, the main and the slave) and the distance between them. The IEEE 802.15.1 standard is based on the Bluetooth v. specifications. 1.x. Bluetooth is a low-cost radio interface with low level power consumption (about 1 mW). At first, the Bluetooth range was within a radius of 10 m, later increased to 100 m. For Bluetooth operation The so-called lower 2.45 GHz ISM (industrial, scientific, medical) band is used, which is intended for the operation of industrial, scientific and medical devices.
IN Bluetooth standard duplex transmission based on time division (Time Division Duplexing - TDD) is provided. The master device transmits packets in odd time segments, and the slave device transmits packets in even time segments (see Time Division Duplex Transmission). Packets, depending on their length, can occupy up to five time segments. In this case, the channel frequency does not change until the end of the packet transmission (see handout Transmitting packets of different lengths)
Package structure (see handout): The standard package consists of an access code, header and information field. The access code identifies packets belonging to the same piconet and is also used for synchronization and query procedures. It includes a preamble (4 bits), a sync word (64 bits) and a trailer - 4 bits of checksum.
The header contains information to control the communication and consists of six fields:
Address (3 bits) - address of the active element;
Type (4 bits) - data type code;
Flow (1 bit) - data flow control, indicates the device’s readiness to receive;
ARQ (1 bit) - confirmation of correct reception;
SEQN (1 bit) - used to determine the sequence of packets;
HEC (8 bits) - checksum.
The final part of the overall package format is the useful information. There are two types of fields in this part: voice field (synchronous) and data field (asynchronous). ACL packets have only a data field, and SCO packets have only a voice field. An exception is the Data Voice (DV) packet, which has both fields. The data field consists of three segments: header useful information, useful information body and possibly CRC (Cyclic Redundancy Check) code
Payload header (8 bits). Only data fields have a payload header. It defines a logical channel, flow control on logical channels, and also has a payload length indicator.
Body of useful information (0-2721 bits). The payload body includes user information. The length of this segment is specified in the payload header length field.
CRC (16 bits). A 16-bit cyclic redundancy code (CRC) is calculated from the transmitted information and then attached to the information. There are 4 types of control packets: NULL, POLL, FHS, ID. They are the same for both ACL and SCO.
ID packets are 68 bits long and are used for paging and querying. Consists of the Access Code field.
NULL packets (126 bits) consist only of the Access Code and Header fields, acting as confirmations of connection establishment or data receipt
The POLL type (126 bits) is similar to the previous one, except that POLL packets oblige the recipient to respond.
FHS packets (366 bits) contain information about the address, device class and clock frequency his transmitter
Security issue in Bluetooth networks: There are also 3 more Bluetooth-specific problems that are widespread in lately: Bluejacking, Bluebugging and CarWhisperer. Bluejacking involves sending some kind of " business cards”, which offer to add a new device to the list of allowed ones. If the user does this without hesitation, the attackers will gain access to the desired object. Bluebugging is an even more dangerous problem that is based on finding security vulnerabilities in technology. If successful, the contents of the device can be accessed without the owner's knowledge. CarWhisperer involves the use of the car's standard audio system, which recently is often equipped with Bluetooth to eavesdrop on conversations inside the cabin.
Institute of Financial and Economic Security
ABSTRACT
Wireless Security
Completed:
Student of group U05-201
Mikhailov M.A.
Checked:
Associate Professor of the Department
Burtsev V.L.
Moscow
2010
Introduction
WEP security standard
WPA security standard
WPA2 security standard
Conclusion
Introduction
Story wireless technologies The transmission of information began at the end of the 19th century with the transmission of the first radio signal and the appearance in the 20s of the 20th century of the first radio receivers with amplitude modulation. In the 1930s, frequency modulation radio and television appeared. In the 70s, the first wireless telephone systems were created as a natural outcome of meeting the need for mobile transmission vote. At first these were analogue networks, and in the early 80s the GSM standard was developed, which marked the beginning of the transition to digital standards, as providing better spectrum distribution, best quality signal, better security. Since the 90s of the twentieth century, the position of wireless networks has been strengthening. Wireless technologies are firmly entrenched in our lives. Developing at tremendous speed, they create new devices and services.
An abundance of new wireless technologies such as CDMA (Code Division Multiple Access), GSM (Global for Mobile Communications, global system For mobile communications), TDMA (Time Division Multiple Access), 802.11, WAP (Wireless Application Protocol), 3G (third generation), GPRS (General Packet Radio Service, packet data service), Bluetooth (blue tooth, named after Harald Blue Tooth, a Viking leader who lived in the 10th century), EDGE (Enhanced Data Rates for GSM Evolution, increased transmission speeds are given for GSM), i-mode, etc. indicates that a revolution is beginning in this area.
The development of wireless local networks (WLAN), Bluetooth (medium and short distance networks) is also very promising. Wireless networks are deployed at airports, universities, hotels, restaurants, and businesses. The history of the development of wireless network standards began in 1990, when the 802.11 committee was formed by the global organization IEEE (Institute of Electrical and Electronics Engineers). Gave a significant impetus to the development of wireless technologies World Wide Web and the idea of working on the Web using wireless devices. At the end of the 90s, users were offered a WAP service, which at first did not arouse much interest among the population. These were the main information services– news, weather, all kinds of schedules, etc. Also, both Bluetooth and WLAN were in very low demand at the beginning, mainly due to the high cost of these means of communication. However, as prices fell, so did public interest. By the middle of the first decade of the 21st century, the number of users of wireless Internet services reached tens of millions. With the advent of wireless Internet communications, security issues have come to the fore. The main problems when using wireless networks are interception of messages from intelligence services, commercial enterprises and individuals, interception of credit card numbers, theft of paid connection time, and interference with the work of communication centers.
Like any computer network, Wi-Fi is a source of increased risk of unauthorized access. In addition, it is much easier to penetrate a wireless network than a regular one - you do not need to connect to wires, you just need to be in the signal reception area.
Wireless networks differ from cable networks only at the first two - physical (Phy) and partly channel (MAC) - levels of the seven-level interaction model open systems. More high levels are implemented as in wired networks, and real network security is ensured precisely at these levels. Therefore, the difference in the security of these and other networks comes down to the difference in the security of the physical and MAC layers.
Although today the protection of Wi-Fi networks uses complex algorithmic mathematical models of authentication, data encryption and control of the integrity of their transmission, nevertheless, the probability of access to information by unauthorized persons is very significant. And if the network configuration is not given due attention, an attacker can:
· gain access to the resources and disks of Wi-Fi network users, and through it to LAN resources;
· eavesdrop on traffic, extract from it confidential information;
· distort information passing through the network;
· introduce fake access points;
· send spam and perform other illegal actions on behalf of your network.
But before you start protecting your wireless network, you need to understand the basic principles of its organization. Typically, wireless networks consist of access nodes and clients with wireless adapters. Access nodes and wireless adapters are equipped with transceivers to exchange data with each other. Each AP and wireless adapter is assigned a 48-bit MAC address, which is functionally equivalent to an Ethernet address. Access nodes connect wireless and wired networks, allowing wireless clients to access wired networks. Communication between wireless clients in ad hoc networks is possible without an AP, but this method is rarely used in institutions. Each wireless network is identified by an administrator-assigned SSID (Service Set Identifier). Wireless clients can communicate with the AP if they recognize the access node's SSID. If there are several access nodes in a wireless network with the same SSID (and the same authentication and encryption parameters), then it is possible to switch mobile wireless clients between them.
The most common wireless standards are 802.11 and its advanced variants. The 802.11 specification defines the characteristics of a network operating at speeds up to 2 Mbit/s. Improved versions provide more high speeds. The first, 802.11b, is the most widely used, but is quickly being replaced by the 802.11g standard. 802.11b wireless networks operate in the 2.4 GHz band and provide data transfer rates of up to 11 Mbps. An improved version, 802.11a, was ratified earlier than 802.11b, but came to market later. Devices of this standard operate in the 5.8 GHz band with typical speeds of 54 Mbps, but some vendors offer higher speeds of up to 108 Mbps in turbo mode. The third, improved version, 802.11g, operates in the 2.4 GHz band, like 802.11b, with a standard speed of 54 Mbit/s and a higher speed (up to 108 Mbit/s) in turbo mode. Most 802.11g wireless networks are capable of handling 802.11b clients thanks to backward compatibility 802.11g standard, but practical compatibility depends on the specific vendor implementation. Most modern wireless equipment supports two or more variants of 802.11. A new wireless standard, 802.16, called WiMAX, is being designed with the specific goal of providing wireless access for businesses and homes through stations similar to stations cellular communication. This technology is not discussed in this article.
The actual range of an AP depends on many factors, including the 802.11 variant and operating frequency equipment, manufacturer, power, antenna, external and internal walls and network topology features. However wireless adapter with a highly directional, high-gain antenna can provide communication with the AP and wireless network over a considerable distance, up to about one and a half kilometers depending on conditions.
Due to the publicly accessible nature of the radio spectrum, there are unique problems with security not available in wired networks. For example, to eavesdrop on communications on a wired network, you need physical access to a network component such as the point at which the device connects to local network, switch, router, firewall or host computer. A wireless network only requires a receiver, such as a regular frequency scanner. Due to the openness of wireless networks, standard developers prepared the Wired Equivalent Privacy (WEP) specification, but made its use optional. WEP uses a shared key that is known to the wireless clients and the access nodes with which they communicate. The key can be used for both authentication and encryption. WEP uses the RC4 encryption algorithm. A 64-bit key consists of 40 user-defined bits and a 24-bit initialization vector. In an attempt to improve the security of wireless networks, some equipment manufacturers have developed advanced algorithms with 128-bit or longer WEP keys, consisting of a 104-bit or longer user portion and an initialization vector. WEP is used with 802.11a, 802.11b and 802.11g compatible equipment. However, despite the increased key length, WEP's flaws (particularly weak authentication mechanisms and encryption keys that can be revealed by cryptanalysis) are well documented, and WEP is not considered a reliable algorithm today.
In response to the shortcomings of WEP, the industry association Wi-Fi Alliance decided to develop the Wi-Fi Protected Access (WPA) standard. WPA is superior to WEP by adding TKIP (Temporal Key Integrity Protocol) and a strong authentication mechanism based on 802.1x and EAP (Extensible Authentication Protocol). WPA was intended to become a working standard that could be submitted to the IEEE for approval as an extension to the 802.11 standards. The extension, 802.11i, was ratified in 2004, and WPA was updated to WPA2 to be compatible with the Advanced Encryption Standard (AES) instead of WEP and TKIP. WPA2 is backward compatible and can be used in conjunction with WPA. WPA was intended for enterprise networks with a RADIUS (Remote Authentication Dial-In User Service) authentication infrastructure, but a version of WPA called WPA Pre-Shared Key (WPAPSK) has received support from some manufacturers and is being prepared for use. in small enterprises. Like WEP, WPAPSK works with a shared key, but WPAPSK is more secure than WEP.